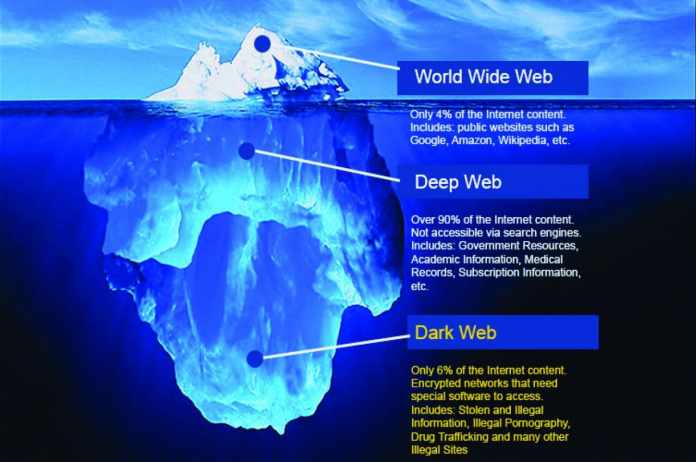
Paderborn. “Nothing is true, everything is allowed” – if you want to look around the deep web out of interest or for a thrill. How to access the dark web You should keep the famous Nietzsche quote in mind. Because as Sebastian Porombka from the University of Paderborn explains: “In the deep web everything could be a fraud. Behind every link there could be a fraudster, a hacker or an undercover agent.” Porombka should know. He is a research assistant and has been dealing with IT security for over ten years. For the NW, he explains what beginners have to consider when surfing the deep web.
Table of Contents
Step 1: Download Tor Browser How to access the dark web
If you want to surf the deep web anonymously and benefit from the encryption of the Tor network, you should download and install a suitable browser. The best known is the Tor browser, which a simple search can find on the net. How to access the dark web Anyone who has installed the Tor browser must first set how strongly their data should be encrypted in the goal network.
Step 2: start the Tor browser. How to access the dark web
The Tor browser looks amazingly unspectacular like a standard Internet browser – it is based on Mozilla Firefox, explains Porombka. How to access the dark web Just what now? Since the file paths in the deep web are encrypted several times, deep web pages cannot be found using standard search engines.
Your URLs consist of wildly jumbled combinations of numbers and letters. They all have the ending .onion – in English onion, because of the layered encoding of the pages. If you want to have a look around, so-called hidden wikis are the first point of contact.
Hidden wikis
Here you can find information and link lists to websites and forums on the deep web. But Sebastian Porombka warns: “In the deep web, anything could be fraud.” Remember: Nothing is true; everything is allowed.
According to Sebastian Porombka, the “Uncensored Hidden Wiki” is a reasonably safe hidden wiki. Here already comes to light what creeps and flies in the depths of the deep web in its most perverse forms. Everything should be easy to find on the Hidden Wiki, drugs, weapons, porn, pictures of naked children. Links promise quick downloads of movies and music.
But Porombka warns: “The same applies here: Everything is potentially fraud. Behind every page there can be a hacker or an undercover investigator.” Simply clicking on it on the deep web can quickly have nasty consequences.
There are also search engines for the deep web that can use to search for specific keywords. One of these search engines is “Not Evil.” After some browsing, Sebastian Porombka presented a website called “Farmer Joe” that supposedly sells marijuana.
Anyone who wants to trade with the site operator has to contact him again in encrypted chat rooms. “Then we are in the Darknet. Anyone who wants to survive here has to come from the criminal scene,” says Poremba. “It works like in gangster films. Payment in secret. For example with the Internet currency Bitcoin. There are dead mailboxes and all that kind of thing.”
German forum
There is also a German forum on the deep web. Under the URL germanyhuscaysx. Information control – no thanks”. This is where users from all over Germany are discussing. About politics, drugs, and freedom of expression – everything allows in terms of content.
Security concerns
Even the most secure encryption via Tor browser and co. Is not one hundred percent confident, says Sebastian Porombka. “It starts with the Tor browser itself. The security certificate is provided by a company called Digicert – and they are based in the USA.” In the event of a threat to US national security, the CIA or NSA could demand access to this program, says Porombka, a member of the Chaos Computer Club (CCC).
A recent alleged major offensive by the CIA on the goal network also raises doubts about whether the Tor users are completely anonymous. The system does not protect against so-called “end-to-end timing attacks”:
Multiple server changes blur the user’s data trail in the Tor network (see infographic). It becomes problematic when the incoming and outgoing servers check.
In this way, a secret service could trace that someone entered the network and at the same time reappeared anonymously at another point. “You can trac back with statistical methods,” says Poremba.
A safer way to sniff around the deep web is the Tails operating system, which is available on CD or downloaded from the Internet. “From this operating system, users can start their computer directly, the Tor browser installed does the rest,” says Poremba. Anyone who starts the Tor browser on their private PC can quickly track it down. The programs and processes that run in the background on the PC access the Internet directly and reveal the user.
Also read: How to stop drinking